Using Vsort to assess threat levels
Introduction
Vsort is a process for assessing the relative risks of vulnerabilities being exploited by different threat actors. It works by defining the threat actors and vulnerabilities separately, and then combining them using the RiskTree Processor. The tools for using Vsort are to be found on the Tools menu.
Defining your threats
Threats are defined in a file that can then be loaded into Designer or Processor for further use.
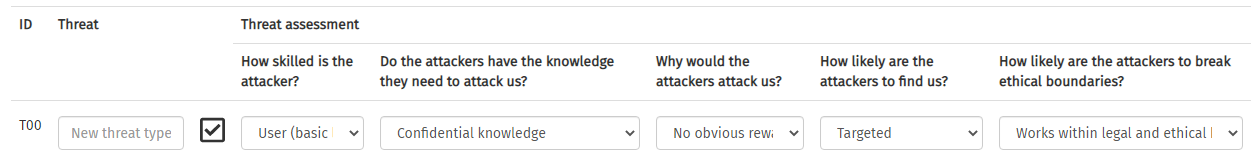
Open the Vsort Threat Selector from the Tools menu. This will start with a blank threat template. The template is populated by specifying the name of the threat, and answering five questions about it. The questions are:
- How skilled is the attacker?
- Do the attackers have the knowledge they need to attack us?
- Why would the attackers attack us?
- How likely are the attackers to find us?
- How likely are the attackers to break ethical boundaries?
To add another attacker, click on the button. This adds a new row into the table.
If you decide not to use an attacker, simply untick the check box to the right of its name. This will exclude it from the Vsort threat file.
To create your Vsort threat file, click on the button. The file, in JSON format, will then be downloaded.
Defining your vulnerabilities
Vulnerabilities are defined in a special type of tag file. The Vulnerability Creator helps you to build this file as quickly as possible.
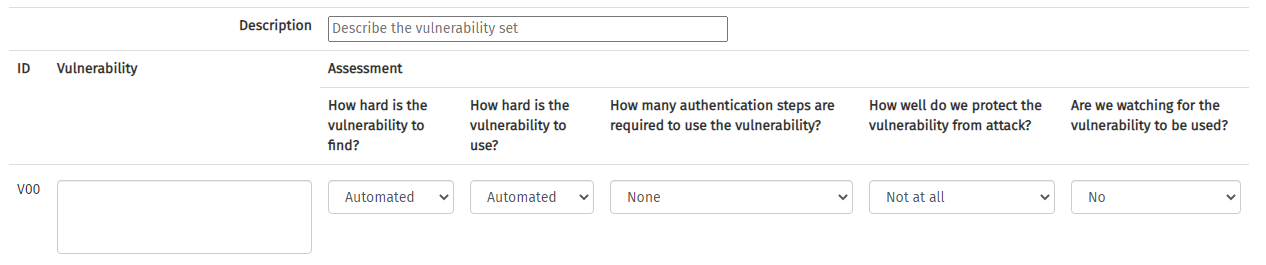
Open the Vsort Vulnerability Creator from the Tools menu. This will start with a blank template, which is populated by describing the vulnerability set (e.g., technical vulnerabilities). Next, you specify the name of the vulnerability, and answer five questions about it. The questions are:
- How hard is the vulnerability to find?
- How hard is the vulnerability to use?
- How many authentication steps are required to use the vulnerability?
- How well do we protect the vulnerability from attack?
- Are we watching for the vulnerability to be used?
To add another vulnerability, click on the button. This adds a new row into the table.
To create your Vsort vulnerability tag file, click on the button. The file, in JSON format, will then be downloaded.
Using Vsort
In order to perform a Vsort threat assessment, you need to tag each of your risks with the vulnerability (or vulnerabilities) that facilitate it. In Designer, load the vulnerability tag file using the Import file tool. Select the file and import it; the number of vulnerabilities in the file will be confirmed. Next, tag each risk (end node) with the relevant vulnerability tags.
Next, you need to apply the Vsort threats to the appropriate branches of the tree. The process for doing this is explained in the Applying threats in Designer page.
Once the threats and vulnerabilities have been applied, when you produce a risk assessment report using the RiskTree Processor, it will use the embedded threat information and vulnerability tags to calculate a Vsort score for each risk, for the threats that you have specified apply to it. These will be shown in the Threats tab.
Related topics
Acknowledgements
Vsort is an open-source project, available at GitHub.