Adding threats to RiskTrees
Introduction
If you are planning on using the threats functionality in the Processor, you will probably want to assign threat sources / actors to different parts of your RiskTree. For example, if you have defined 'Users' as one of your threats, you will only want this to affect branches of your tree that contain risks that could come about from user actions. In order to do this, you will need to apply the threats to your RiskTree.
Loading a threat file
To start applying threats, you will need to load your threat file. This is a JSON format file created using the Threat Selector tool, or the Vsort Threat Selector tool, both of which are found on the Tools menu. Assuming that you have created the necessary threat file, in Designer you need to select Apply threats button from the Designer menu.
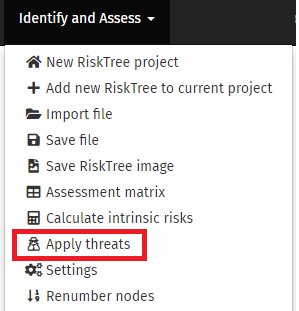
You will be prompted to select the threat file and import it. Click on the 'Choose file' button to open the file selection dialogue box, then the 'Import' button.
The threats are now loaded and available for use.
You can only load one threat file for a RiskTree. If you load a second file, its threats will replace those of the previous file, and all previous threats on nodes will be removed.
Applying threats to nodes
To assign a threat source / actor to a node, select the Threats option from the node menu:
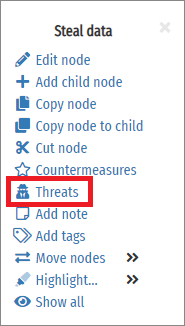
This will open the Threat Selection box:
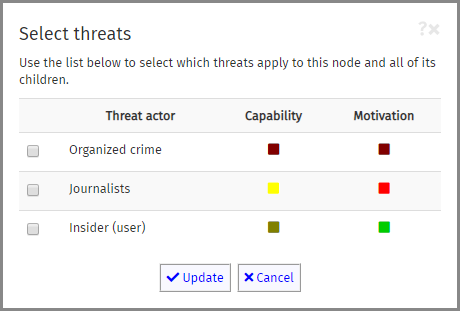
You can select the threat(s) appropriate to this tree branch (i.e., this node and all of its children) by ticking the checkbox to the left of the threat name. The coloured squares to the right of the name give you a quick view of the Capability and Motivation of the threat.
If a threat has already been selected on a node higher up the tree from the currently selected node, you will see that it is already ticked, and the checkbox is disabled, preventing you from unticking it - it has been 'locked' on. This is because threats affect every child node as well as the node on which they have been chosen. In the example below, the 'Insider (user)' threat has been locked.

The risk assessment report
When you load a RiskTree with threats into the Processor, if it is the only RiskTree being loaded then you do not need to select the threat file separately – the threats embedded into the RiskTree file will be processed automatically.